Public Key Infrastructure (PKI)
Public Key Infrastructure: Build Trusted Identity and Enable Authorized Access
New Concept of “Public Key Infrastructure”….Our entire ecosystem is devoted to digital certificates and encryption.
This ecosystem encompasses, not just the software and hardware, but all of the people involved with the digital certificates. PKI certificates are issued from a CA (certificate authority), which creates and manages them. Each PKI certificate is a unique identifier and greatly aids in creating trusting relationships between customers and businesses. The creation and management of the PKI can be handled in-house or via a management company.
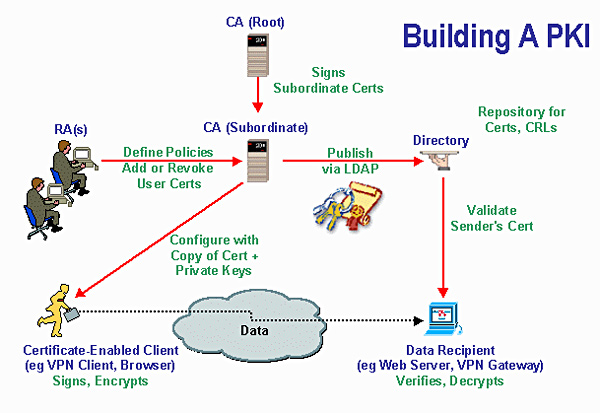
An effective PKI is transparent.
PKI is the foundation on which secure and trusted transactions can be executed. Through PKI, we manage keys and certificates for an organization to establish and maintain a trustworthy networking environment. A PKI enables the use of encryption and digital signature services across a wide variety of applications.
The PKI approach to security does not take the place of all other security technologies; rather, it is an alternative means of achieving security.
Cloud services, IoT driving up use of PKI applications:
The Internet of Things is playing an increasingly important role in influencing public key infrastructure planning and usage, according to a new report from the Ponemon Institute sponsored by cyber security vendor Thales eSecurity. PKI use is increasing due to the growing impact of the Internet of Things (IoT). PKIs, which are used for authentication, digital signing, and encryption, are a core service supporting a variety of use cases and applications.
PKI AND CREDENTIAL MANAGEMENT “Go hand-in-hand”
Controlling access is the heart of any enterprise security environment—making sure only those who have the appropriate permissions can access your data, enter your facilities, print a secure document, etc.
Public Key Infrastructure (PKI) uses key pairs and certificates to verify the identity of users and systems. The digital certificate links the name of an individual to their public key.
A PKI environment assigns a digital identity for all your employees and machines, allowing for secure access to data, networks and physical locations. The PKI environment includes Credential Management solutions for complete lifecycle administration of certificates and permissions.
The need to securely and timely manage users and authenticators is important with any PKI-based deployment. Our preferred partners offer the most comprehensive identity access and Credential Management systems to administer, monitor, and manage strong authentication deployments and digital signing across the organization.
Gaugeable Benefits
- PKI is a standards-based technology and allows choice of trust provider – Couple of advantages of PKI has led to its emergence as an industry standard for securing Internet and e-commerce applications.
- Highly Scalable – Users maintain their own certificates, and certificate authentication involves exchange of data between client and server only. This means that no third party authentication server needs to be online.
- Enablement of Single Sign becomes feasible – Although PKI is not notably a single sign-on service, it can be implemented in such a way as to enable single sign-on.
- Trusted Identity Solution – PKI-enabled applications can save time and effort, while at the same time reduce costs. It also has the potential to user in transparency and accountability, authenticating identities and communicating sensitive information online.The benefits accrued to the end-users would therefore be enormous, and lends itself as a strong technology component in a Digital India.
- Trusted Security Leader – We envisage PKI to have an impressive impact on our complete ecosystem, as its main purpose is to facilitate the secure electronic transfer of information for a range of network activities such as e-commerce, internet banking and confidential emails.
- Flexible Operational Models – PKI is available in either a Managed PKI or an On-Premise model. These options allow you to select the PKI solution that best fits your needs for cost effectiveness, security, and control.
Open way for Higher Value into your Core Business
By leveraging digital technologies, we can transform your current operations into new processes that will allow you to transform real-time insights into your innovation processes, to enhance speed of development of offerings and take them to market faster and more economical than ever.
To strengthen valuable customer relationships, all these processes with customer and partner and ecosystem should be integrated well.
